Zerodays - CVE patching using RVTools, streamlit, python, docker and ansible
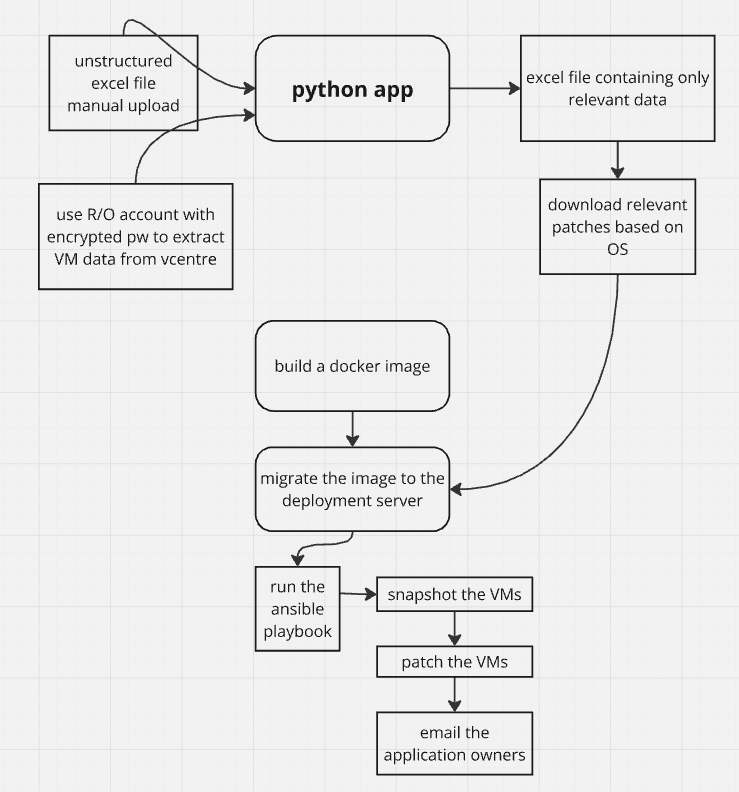
A python app using streamlit is developed to speed up extracting relevant information from a standard excel file. The information is then passed to a ansible running in a container to patch the vulnerable virtual machines.
DOCKER
Jack Jalali
11/2/20243 min read


Task:
Automate the extraction of relevant data from standard excel files listing vulnerable virtual machines. Pass the extracted data to an ansible container which is then used to patch the vulnerable virtual machines.
Prerequisites:
vscode
RVTools (https://www.robware.net/)
docker
ansible
Method:
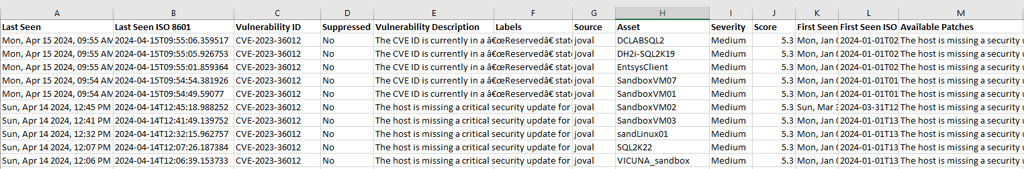
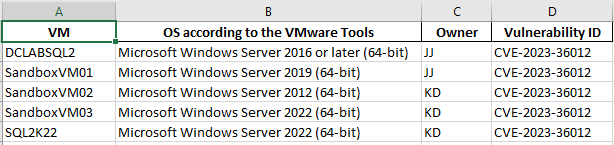
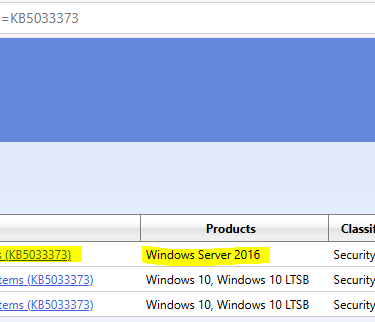
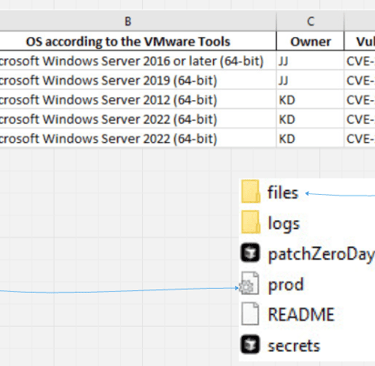
The InfoSec team regularly sends email notifications that include attachments detailing vulnerabilities within our virtualised infrastructure. Unfortunately, these attachments often contain unnecessary information, such as powered down or decommissioned VMs. An example of a typical attachment is shown below:
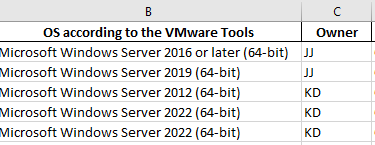
However, I'm only interested in powered on VMs, their owners and the version operating system they are running and the Vulnerability ID. I need to know who the server owners are because they will be responsible to reboot their servers if necessary and verify that their applications are ok after the patches are applied. :
The current process of reviewing attachment lists can be labour-intensive and time-consuming, with numerous items to sift through. Automating this task would greatly improve efficiency and reduce the risk of human error.
An application based on python and streamlit is developed that takes as input the "dirty" excel file sent by the infoSec team, then runs the RVTools and compare and extract only the relevant data as described above.
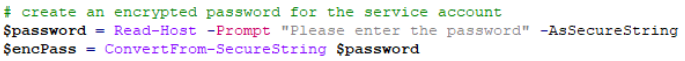
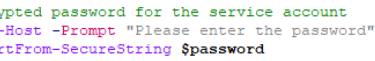
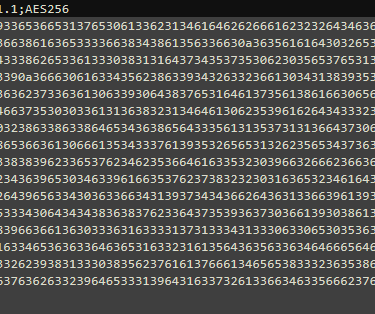
First encrypt the password for the read-only vCentre account, this account is used to run the RVTools (https://resources.robware.net/resources/prod/RVTools.pdf) and extract the data which is then used to compare with the uploaded excel file.
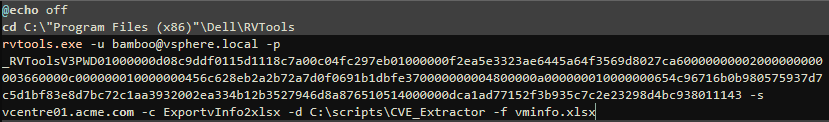
The batch file that runs RVTools that only extracts vinfo from the vCentre is listed below:
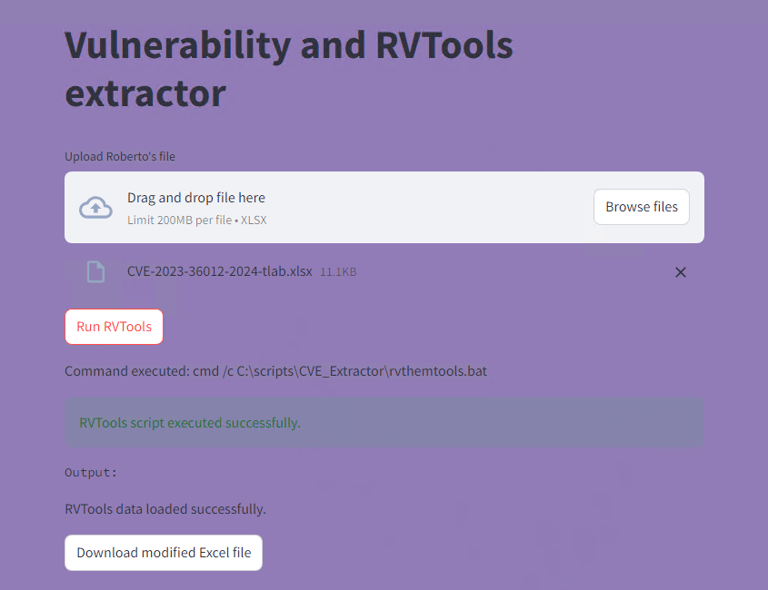
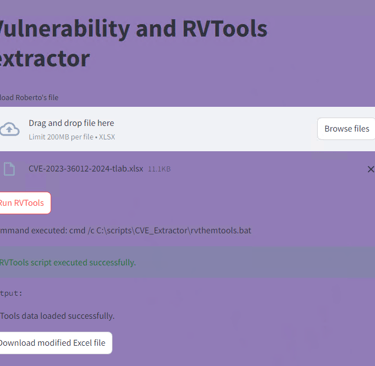
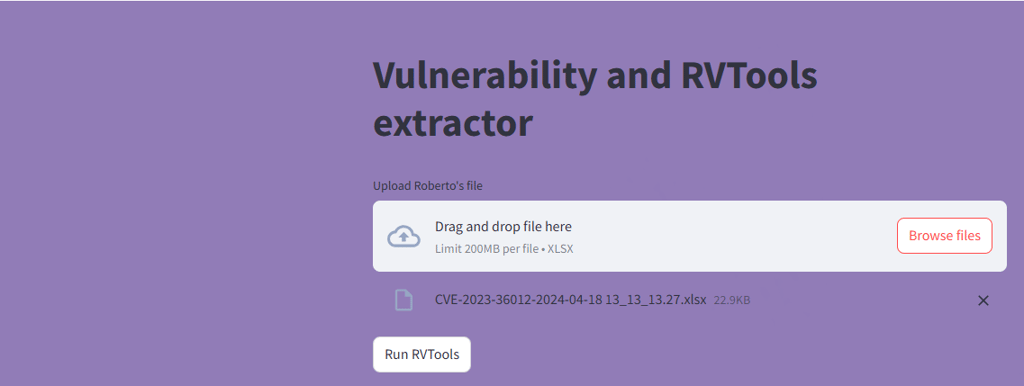
The user interface for the app is show below:
upload the unstructured file, and run the RVTools:
Once the processing is done, the app will allow you to download the processed file:
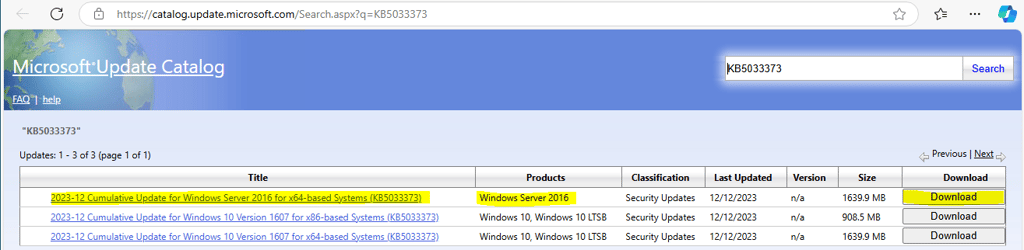
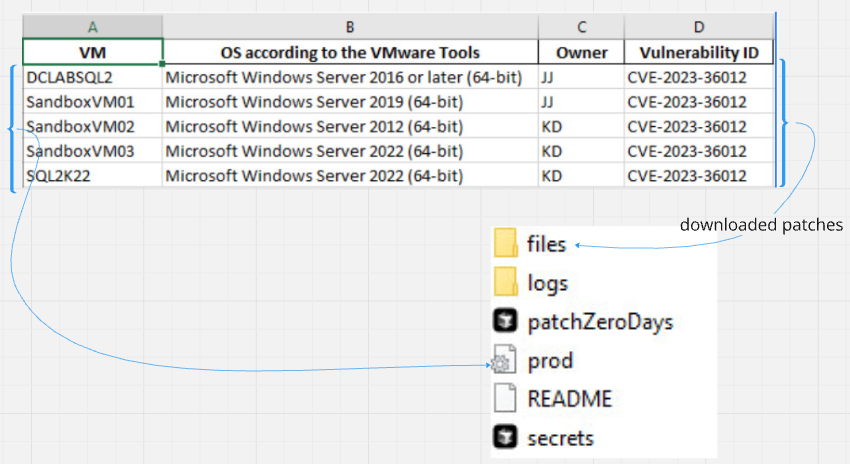
Now that we have the vulnerability ID(s) and the corresponding operating systems we can download the relevant CVEs from:
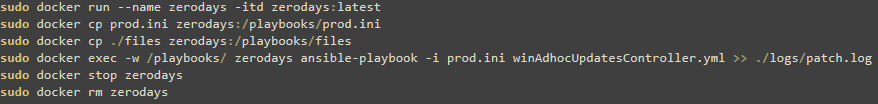
All downloaded patches can now be copied to the "files" folder within the server running the ansible docker container. The list of VMs from the processed excel file goes into the ansible inventory file called prod.ini as shown below.
the patchZeroDays.sh shell file, when executed triggers the launch of a container called zerodays based on the docker image zerodays:latest. As part of this process, the script copies the ansible inventory file, prod.ini together with the contents of the files folder to the container. The container then executes an Ansible playbook (winAdhocUpdatesController.yml) to apply the latest patches, capturing all relevant output and logs in the patch.log file for future reference.
After the successful execution of the ansible play book the docker container is stopped and removed.
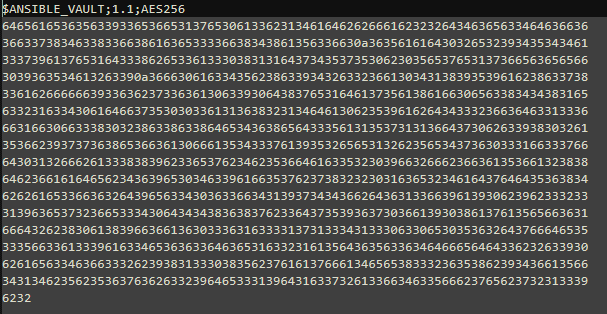
all sensitive data like usernames and passwords are included in the encrypted secrets.yml file:
The ansible playbook snapshots each VM before installing the patches and when done, it emails the VM owners informing them that their servers have been patched. Owners can then verify the health of their VMs and can rollback the status of the servers by reverting back to the snapshots.
How ansible docker image was created will be explained in later post. The code for the python application can be found in my github