Deploy N8N on Azure Kubernetes with autoscaling
AKS + AGIC + n8n + HTTPS self-signed
CLOUD
Jack Jalali
9/1/20254 min read
Introduction
The idea behind this post was to come up with a framework or a procedure to deploy web applications, in this case n8n, to Azure and run it on Azure Kubernetes (AKS) using Azure-native services only, with web apps being exposed over HTTPS via a self-signed TLS secret.
The design supports multi-tenant n8n deployments, by assigning each one a separate namespace and ingress host. This design should be very useful for AI automation consultants to host multiple n8n applications and adapt to traffic load.
Prerequisites:
Azure CLI and OpenSSL - preferably running in a docker container
Azure subscription owner/contributor rights
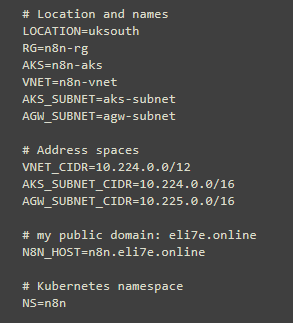
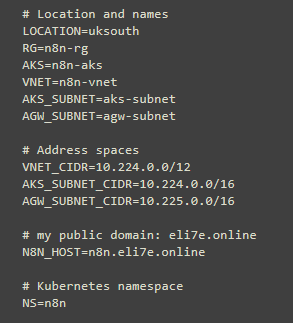
Define the Variables:
variables can be validated after entry like:
echo $RG $AKS $N8N_HOST
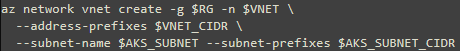
1- create the resource group and VNet:
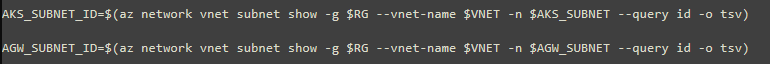
VNet and AKS subnet:
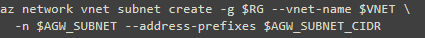
create a dedicated app gateway subnet:
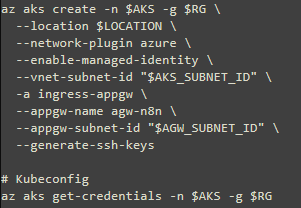
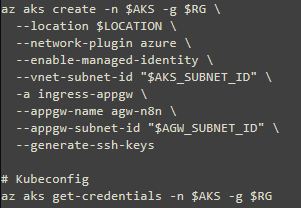
2- Create AKS with the AGIC add-on:
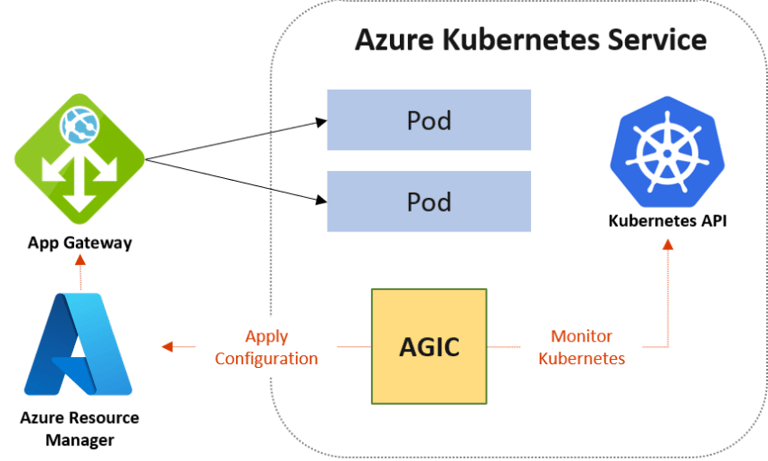
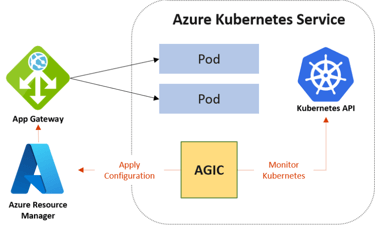
The Application Gateway Ingress Controller (AGIC) is a Kubernetes application, which makes it possible for Azure Kubernetes Service (AKS) customers to leverage Azure's native Application Gateway L7 load-balancer to expose cloud software to the Internet.
AGIC helps eliminate the need to have another load balancer/public IP address in front of the AKS cluster and avoids multiple hops in the data path before requests reach the AKS cluster. Application Gateway talks to pods using their private IP address directly. This capability also brings better performance to the deployment.
How to enable AGIC add-on for an existing AKS cluster with an existing application gateway was taken from this tutorial.
using the existing subnet, above:
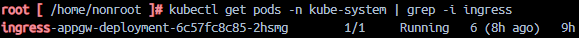
to see if AGIC is running:
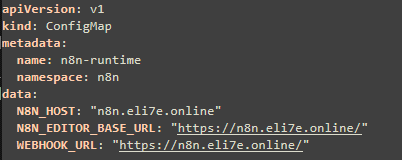
3- Namespace, ConfigMap, Secrets and Storage:
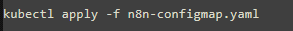
n8n-configmap.yaml
run the yaml file:
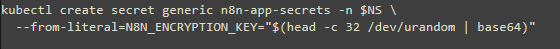
encryption secret for n8n:
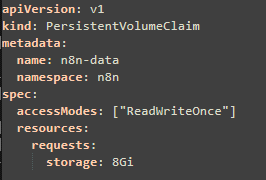
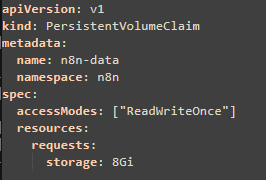
the yaml file to create the persistent data, n8n-pvc.yaml:
execute the above yaml file:
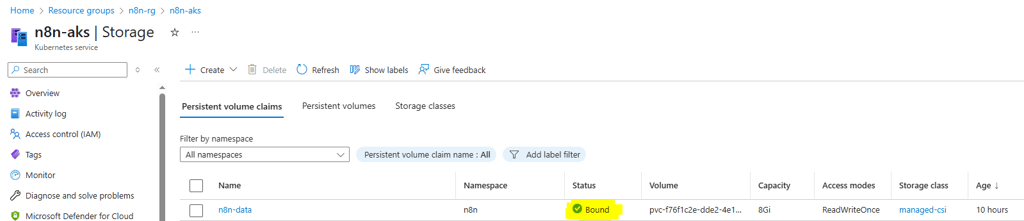
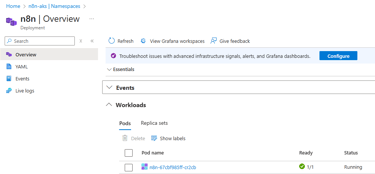
The status of the PVC should show "Bound":
4- Deploy n8n:
I'm going to use the official image registry, and I'm going to use two official n8n API endpoints to check the status of both the instance and the status of the database: /healthz, healthz/readiness. The yaml file to deploy n8n is n8n-deploy-svc.yaml. All config files can be accessed from my github.
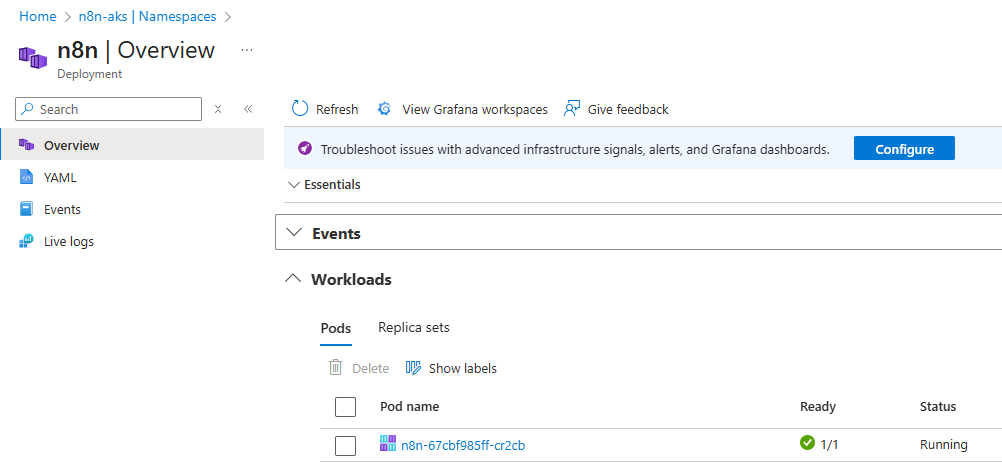
Once deployed, the status of the pod can be checked:
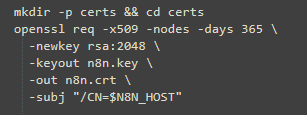
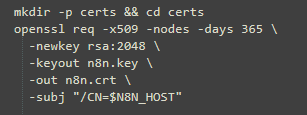
5- Generate self-signed certificate and TLS secret:
The public/private key pair must be created first. The public key certificate must be .PEM encoded and match the given private key.
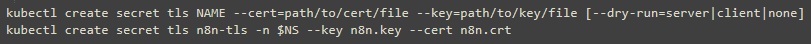
Then we can create a TLS secret from the given public/private key pair, see this site for reference.
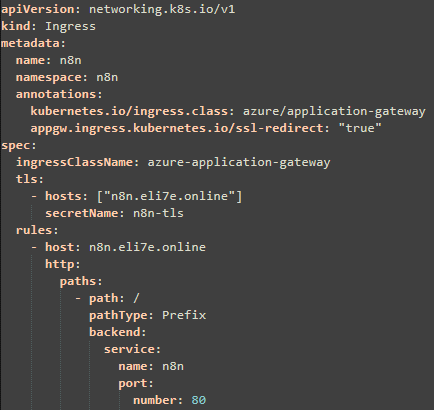
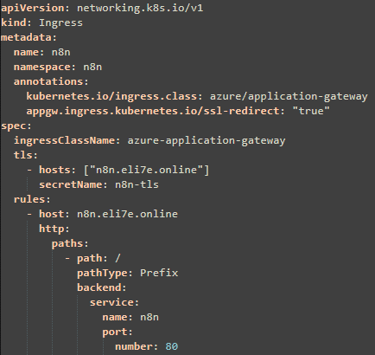
6- Ingress (AGIC) with HTTPS and redirect:
Application Gateway can be configured to automatically redirect HTTP URLs to their HTTPS counterparts. When this annotation is present and TLS is properly configured, Kubernetes Ingress controller will create a routing rule with a redirection configuration and apply the changes to your App Gateway. The redirect created will be HTTP. Reference.
deploy the n8n ingress yaml file:
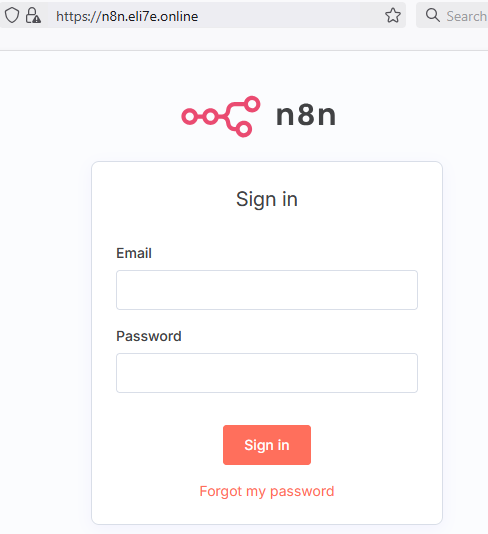
7- test the installation:
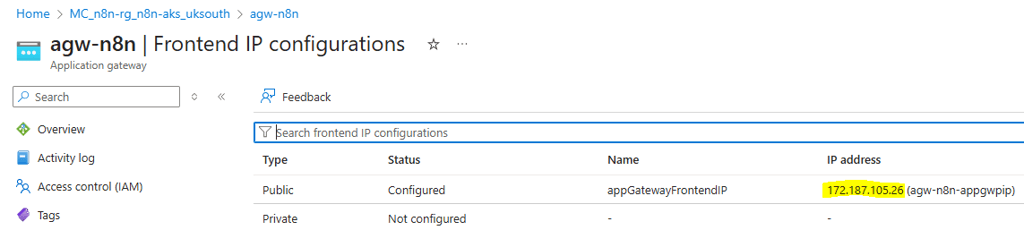
find out the public IP assigned to the App Gateway:
we can now either create an A record for $N8N_HOST in our domain provider or as a quick test we can create an entry in our local host file:
"C:\Windows\System32\drivers\etc\hosts"
172.187.105.26 n8n.eli7e.online