Certificate Management System
Application Automation and Knowledge Transfer
AUTOMATION
Jack Jalali
8/25/20253 min read


Introduction
At work, my colleague and I often dealt with certificate requests - generating CSRs, creating PFX files, and setting up self-signed certificates for services like IIS.
After a while, we decided enough was enough. Instead of being the “certificate helpdesk,” we automated the whole process and built a self-service portal. Now anyone in the firm can generate what they need without having to know (or care) about the steps behind it. For us, it means fewer pings on Teams and more time for the work that actually matters.
The interesting part is this isn’t just automation—it’s knowledge transfer. What used to sit with a couple of people is now available to everyone. And because we designed it around the 99% of requests we actually get, it’s tailored to our environment. The best bit? We saved the firm thousands by not buying bloated off-the-shelf software full of features nobody would ever use.
Application Statement
Build a comprehensive web application for generating Certificate Signing Requests (CSRs), private keys, Personal Information Exchange (PFX) files and creation of self-signed certificates using OpenSSL.
Application Flow
Use the following OpenSSL command to generate the private key and CSR:
openssl.cfg can be created from scratched, but we have a config that we have been using so I have provided it to the application as a reference file.
Use the following OpenSSL command to generate the pfx file:
Verify the CSR using:
Verify the PFX file using:
Post-Processing
Copy both <certificate_name>.csr and <certificate_name>.key to:
C:\scripts\certs
Email the user (user_email) with the file location of the CSR, the verification result (openssl req -in <certificate_name>.csr -noout -text)
Implementation Details
Use Python’s sub process module to execute OpenSSL commands safely.
Implement strong error handling for common issues such as missing configuration files or failed OpenSSL commands.
Provide clear Streamlit messages to confirm success or highlight errors.
Send emails using a dependable method such as smtplib.
Keep the code modular, easy to read, and ready for production.
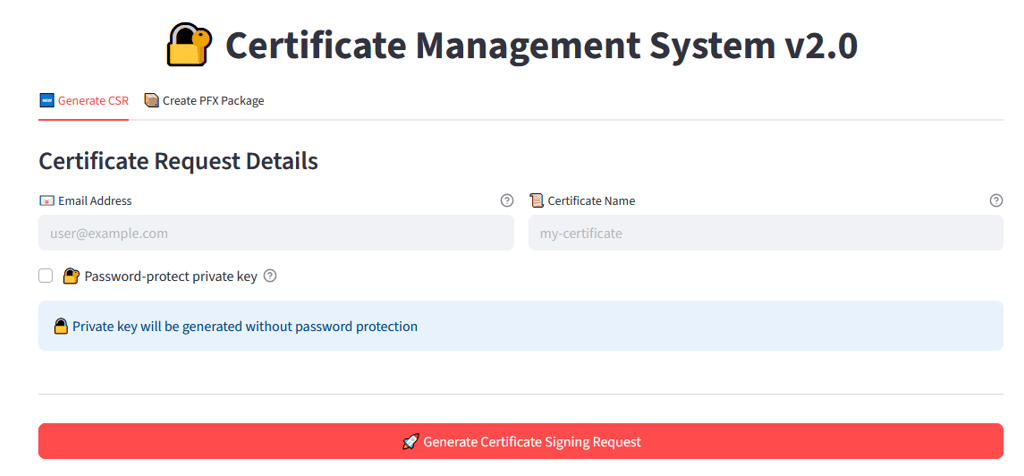
Application layout
The application generates Certificate Signing Requests (CSRs) based on a user-defined certificate name. Users can choose whether to password-protect the private key. After the CSR is created, the application displays the certificate details and verification results to confirm the certificate is valid and free from corruption.
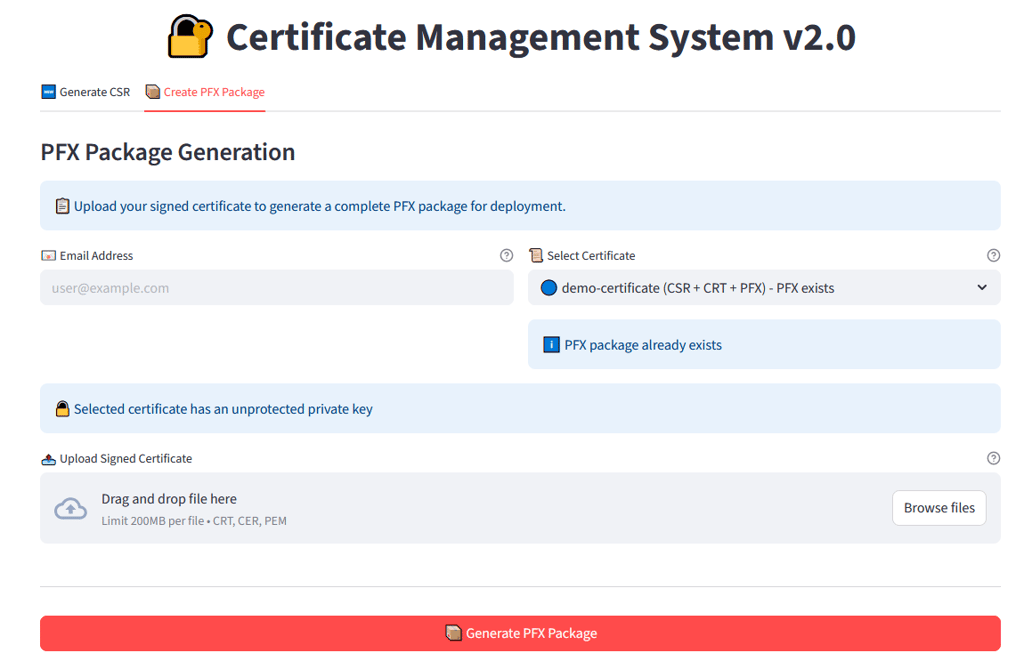
Once the certificate is back from the certificate authorities like DigiCert etc. the user can application to generate the PFX package:
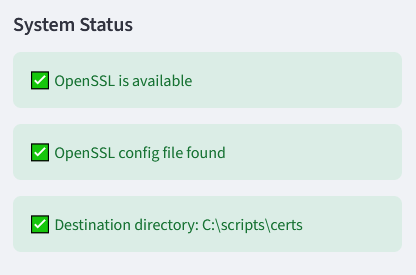
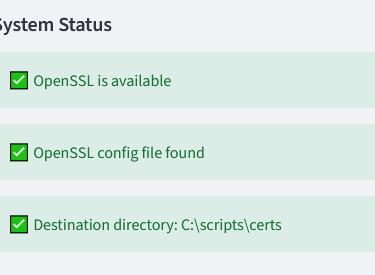
some system checks are built in to the app:
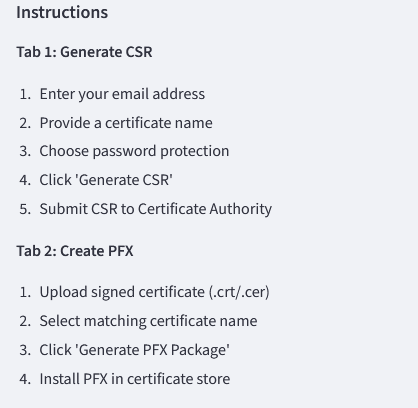
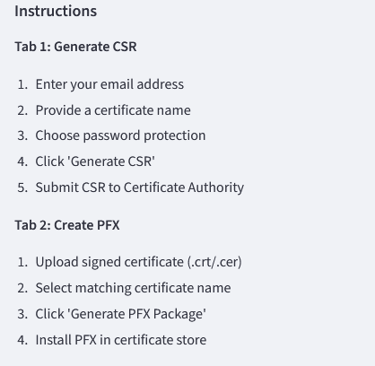
together with instructions on how to use the app:
more functionality will be added in future versions. The complete code can be viewed in my github.
openssl req -new -newkey rsa:2048 -nodes -keyout <certificate_name>.key -out <certificate_name>.csr -config <cert.conf>
openssl.exe pkcs12 -export -out <certificate_name>.pfx -inkey <certificate_name>.key -in <certificate_name>.crt
openssl req -in <certificate_name>.csr -noout -text
openssl.exe pkcs12 -in <certificate_name>.pfx -info -noout